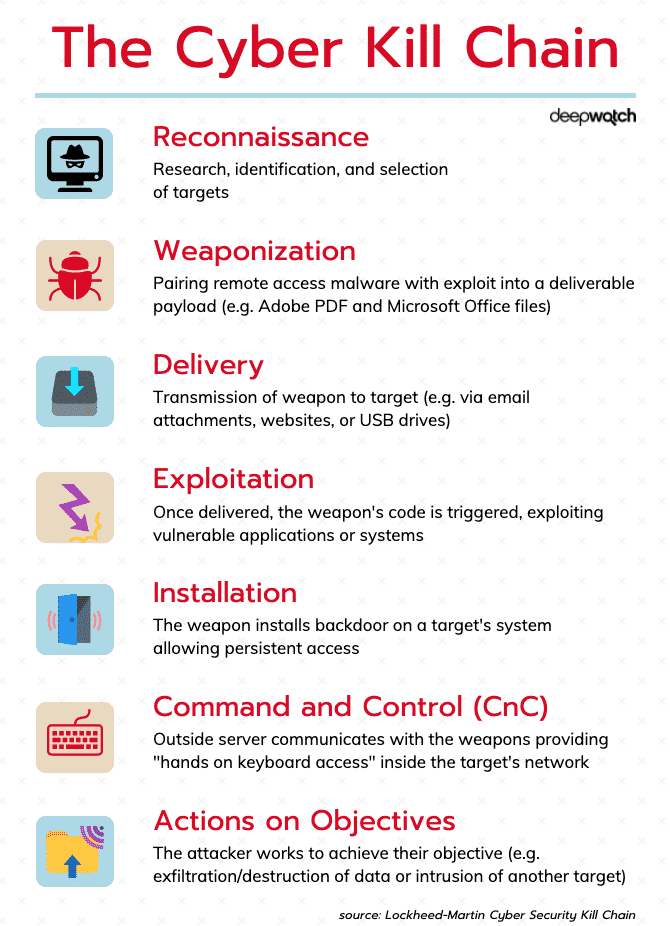
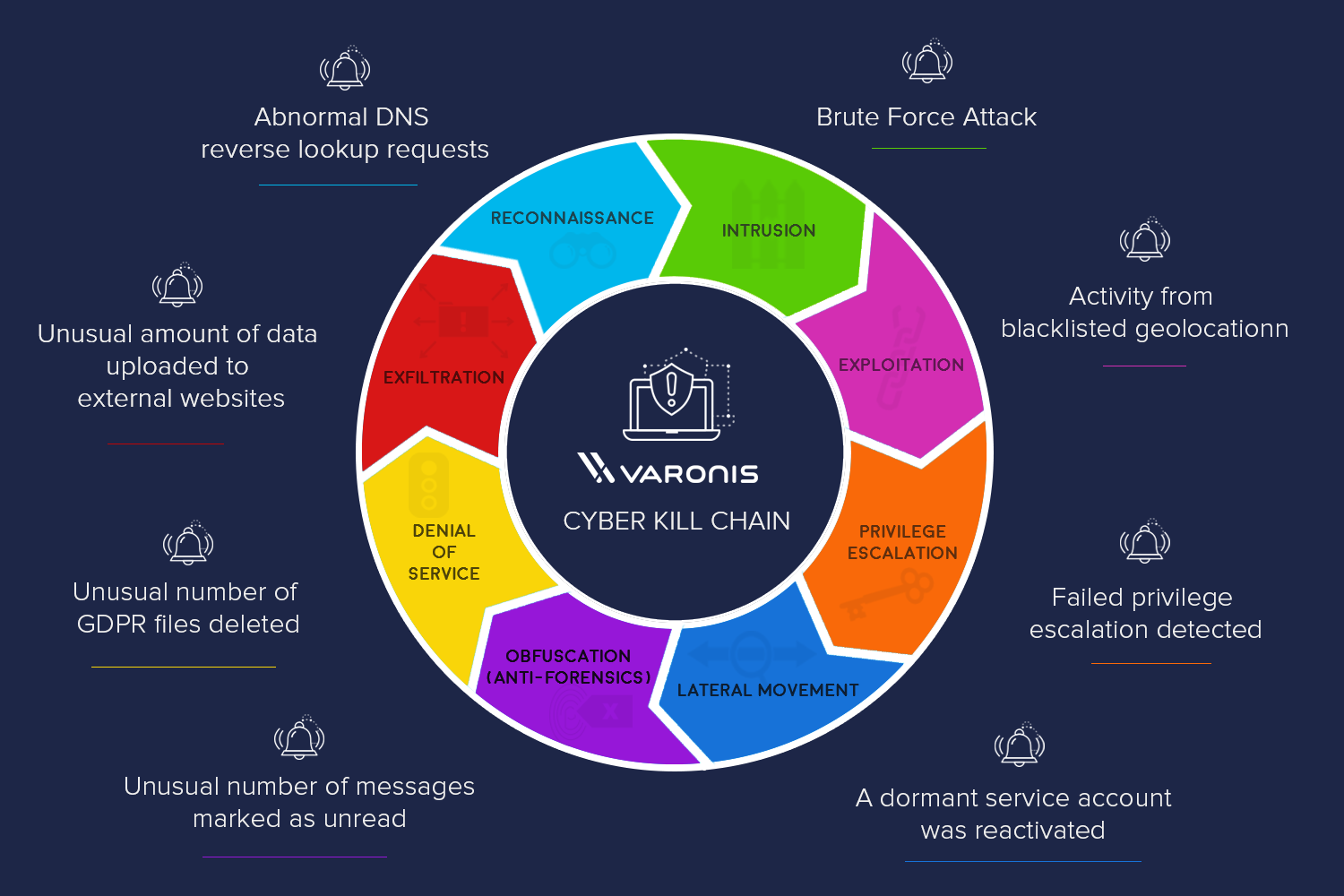
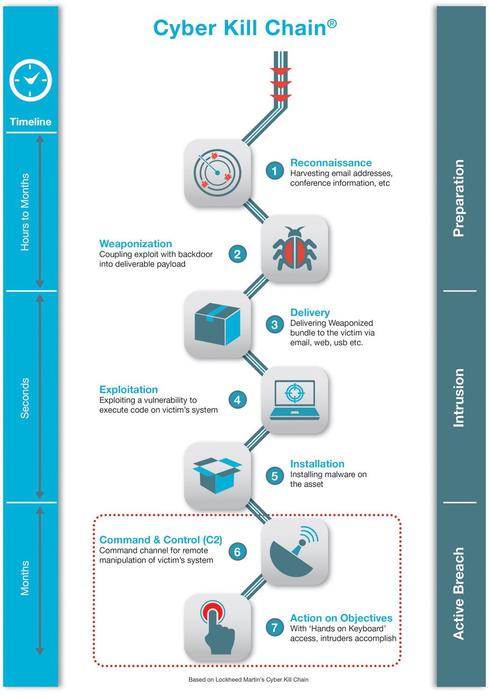
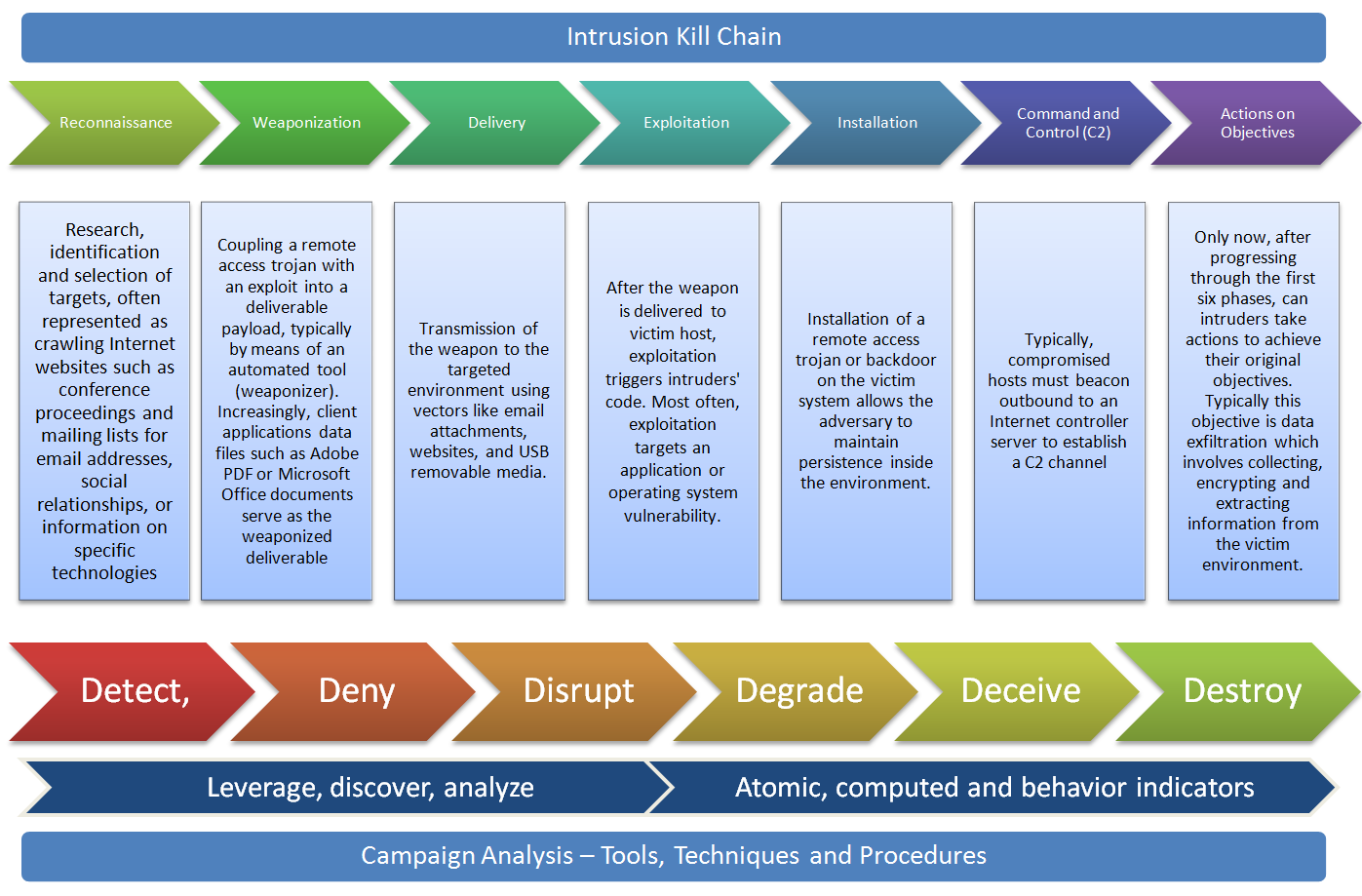
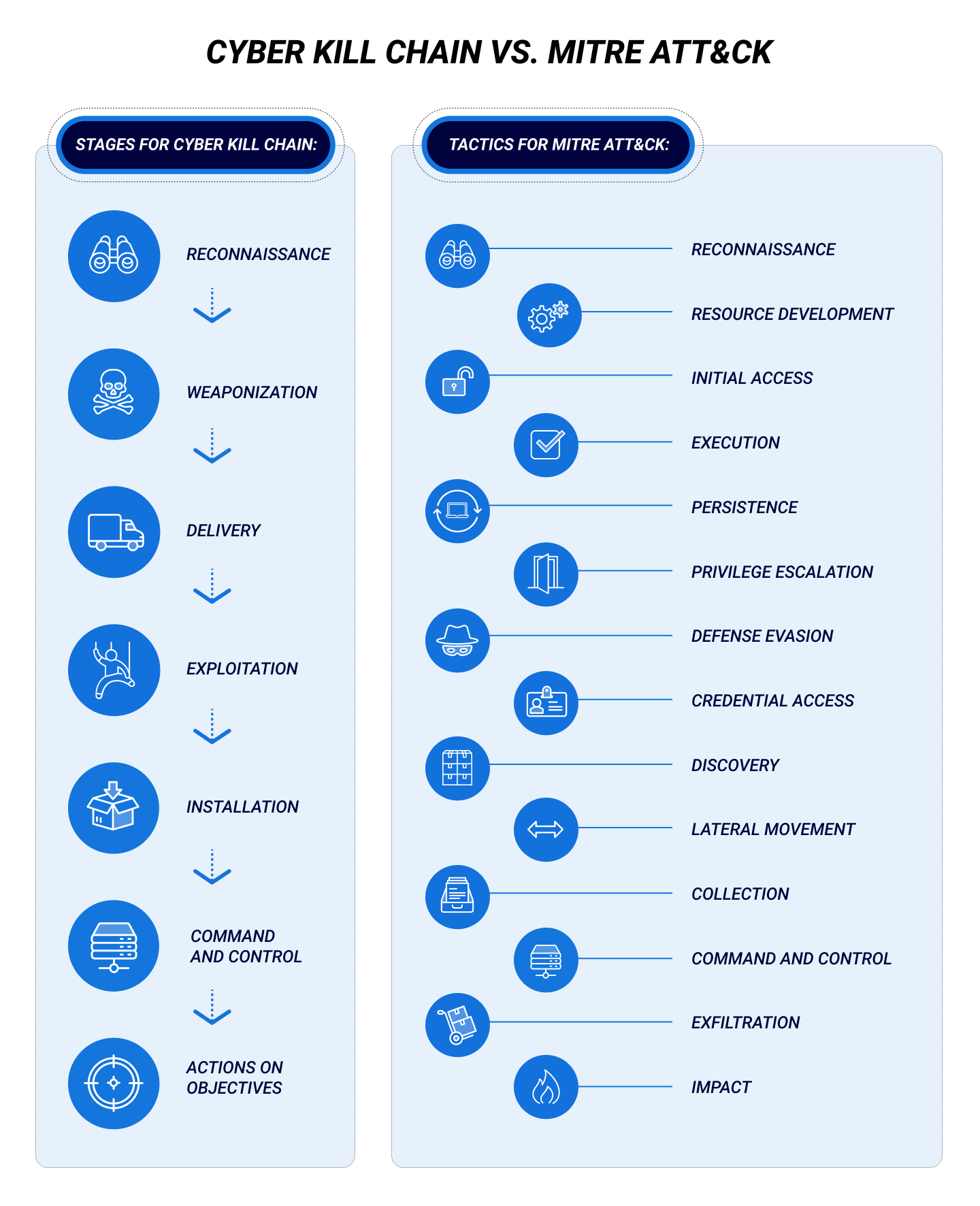
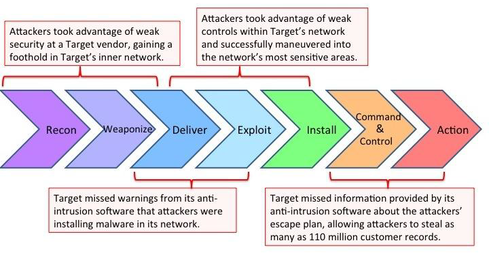
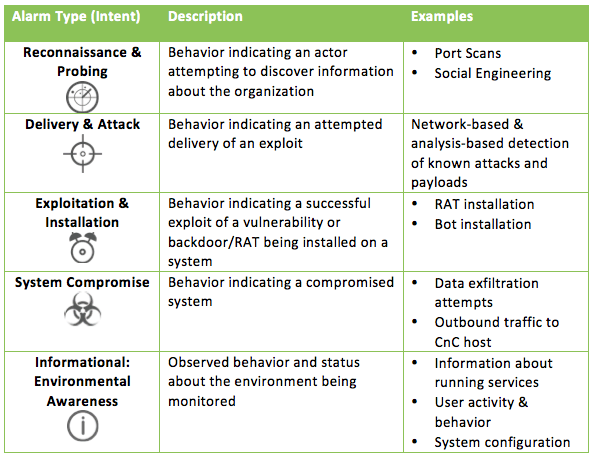
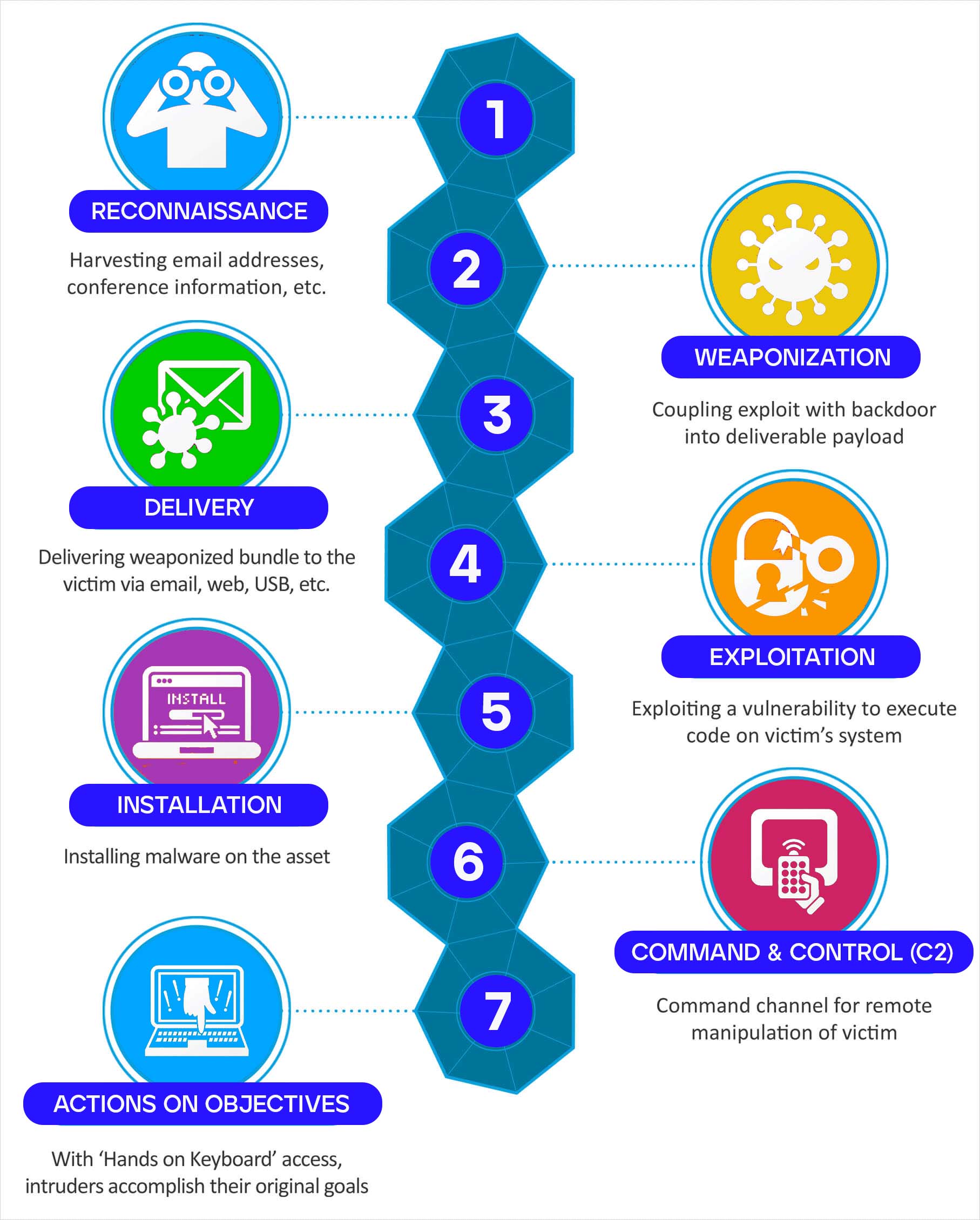
![PDF] A novel kill-chain framework for remote security log analysis with SIEM software | Semantic Scholar PDF] A novel kill-chain framework for remote security log analysis with SIEM software | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/f57e5ba0d4da5b0aed0d0816df4af5ee171746ae/18-Figure1-1.png)
PDF] A novel kill-chain framework for remote security log analysis with SIEM software | Semantic Scholar
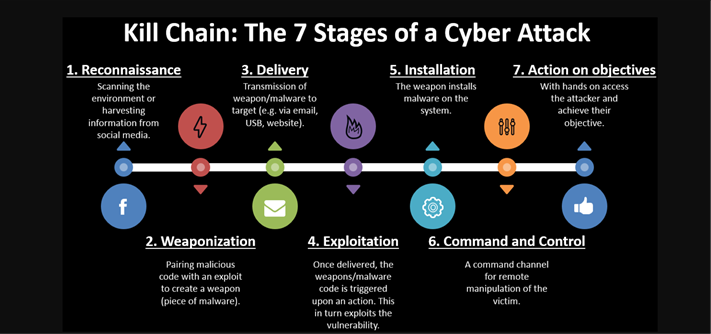
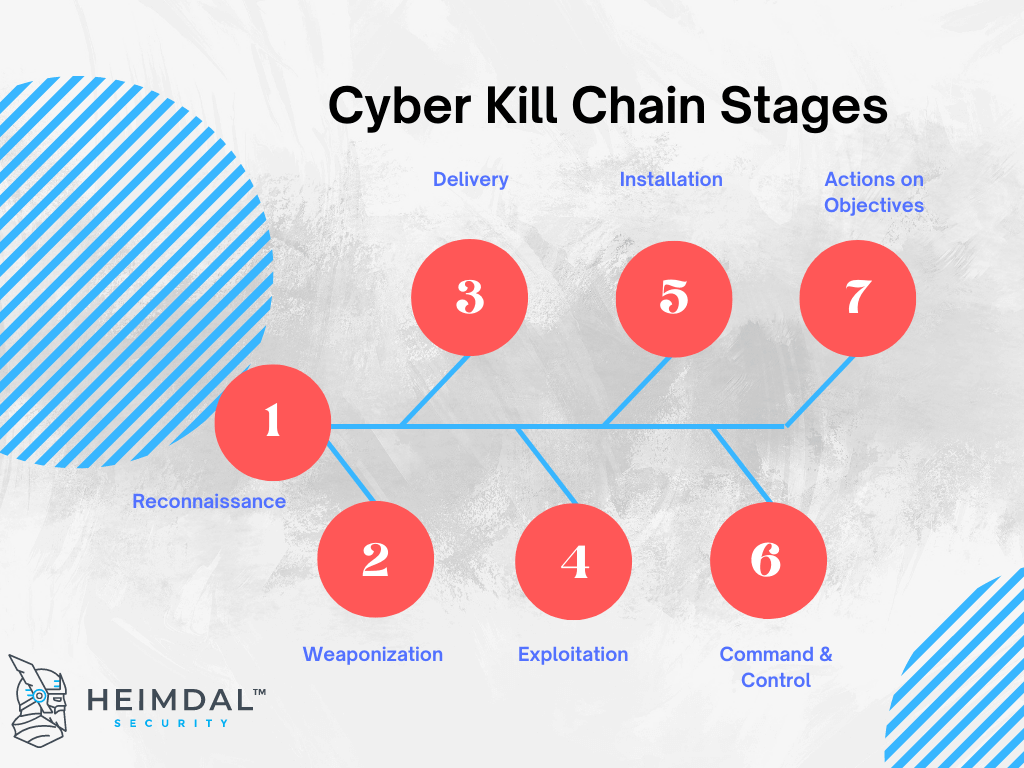
Applied Explanation of the “Cyber Kill Chain” Model as a Cyber Attack Methodology | by Ibrahim Akdağ| Ph.D. | Medium

MCKC: a modified cyber kill chain model for cognitive APTs analysis within Enterprise multimedia network | Multimedia Tools and Applications

View of Railway Defender Kill Chain to Predict and Detect Cyber-Attacks | Journal of Cyber Security and Mobility
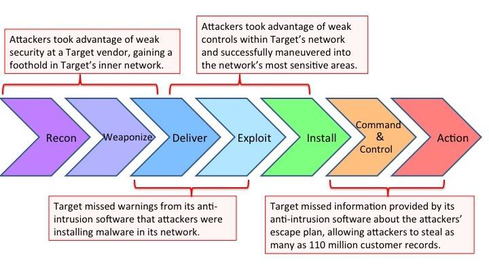
![Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram Lockheed Martin Cyber Kill Chain (CKC) [22] seven steps. The part that... | Download Scientific Diagram](https://www.researchgate.net/publication/335024682/figure/fig1/AS:789313017098241@1565198296990/Lockheed-Martin-Cyber-Kill-Chain-CKC-22-seven-steps-The-part-that-is-specified-with.png)